Our research group aims to design, implement, and make novel system software stacks available for new computation paradigms through operating system, hypervisor, and hardware-software co-design.
NOTE: We’re looking for students who want to write BSc/MSc theses or participate in Guided Research. If you are interested, please check the application instructions.
Current Active Projects
# Secure and Efficient Confidential Virtual Machines
Confidential Virtual Machines (CVMs) are emerging trends that offer protection of data in use, allowing for trusted computation on remote, untrusted infrastructure in the cloud. While CVMs are gaining attention thanks to their deployability, the traditional system software stacks incur performance overhead due to the limitations of CVMs, especially for I/O. Therefore, we need to rethink software stacks to achieve efficient yet secure computation.
This project analyzes CVM software stacks to reveal the current bottleneck of the system software stack and proposes a novel design to optimize it while keeping the security guarantee.
Keywords: Virtualization, TEE, AMD SEV-SNP, Intel TDX, Arm CCA
Publication
- Wallet: Confidential Serverless Computing
Patrick Sabanic, Masanori Misono, Teofil Bodea, Julian Pritzi, Michael Hackl, Dimitrios Stavrakakis, Pramod Bhatotia
NSDI 2026
[Arxiv] - Confidential VMs Explained: An Empirical Analysis of AMD SEV-SNP and Intel TDX
Masanori Misono, Dimitrios Stavrakakis, Nuno Santos, Pramod Bhatotia
SIGMETRICS 2025 / ACM POMACS 2024
[Paper] [Abstract] [Presentation] [Code]
Thesis / IDP
| 2024 | Performance Analysis and Optimization of Confidential Virtual Machines | Luca Mathias (BSc) |
| 2023 | cvm-io: Secure High-Performance Storage Stack for Confidential Virtual Machines | Robert Schambach (MSc) |
# Hyper-scale Virtual Networking
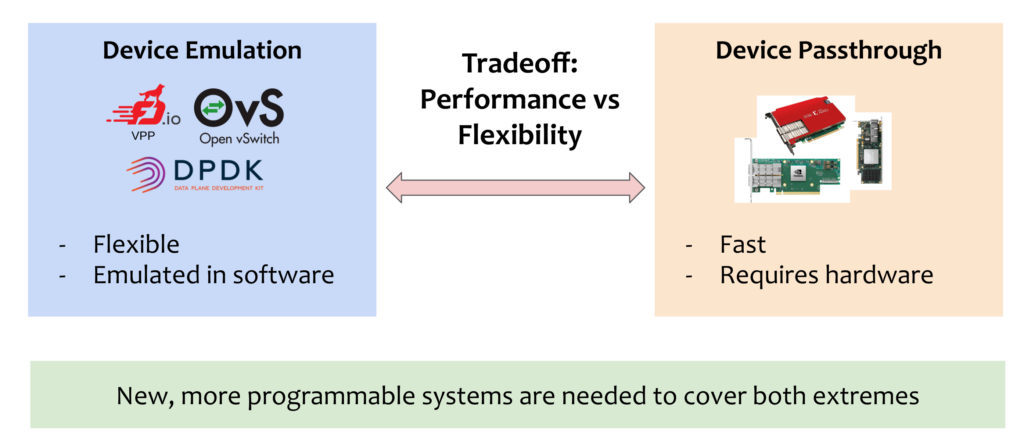
Virtual Machines (VMs) are not only widely used in clouds to isolate tenant workloads, but increasingly also to deploy Virtual Network Functions (VNF). From these use cases emerges a need for flexible, scalable, and fast IO. The current industry standard is, however, either not flexible nor scalable (passthrough + SR-IOV), or has high overheads (software switch + vhost). To address these issues, we are striving to improve network virtualization stack architectures so that we can implement sophisticated multiplexing strategies for VMs in software without compromising performance, dependability, or security.
Keywords: Data center networking, VirtIO, SmartNIC, Performance
Thesis / IDP
| 2025 | vDPDK: A Para-Virtualized DPDK Device Model for vMux | Dominik Kreutzer (MSc) |
| 2023 | Hyper-scalability of Network Interface Cards for Virtual Machines | Florian Dominik Freudiger (BSc) |
| 2022 | Automated Measuring of Ioregionfd and vMux Performance | Sandro-Alessio Gierens (GR) |
| 2022 | Rethinking IO emulation architectures for VMs | Sandro-Alessio Gierens (BSc) |
# Co-design of OS with High-Performance Applications
Kernel-bypass and userspace components have been the preferred way to fully harness the performance of modern computing systems. This paradigm moved OS services to userspace, including scheduling (ghOSt [SOSP’21]) and IO (DPDK/SPDK, RDMA). However, while being theoretically the most performant in terms of speed/latency/etc, kernel-bypass has several limitations, including the lower sharing of resources and the increased complexity in the application.
Instead of moving OS services to userspace, we propose to redesign them to strive to achieve the same performance and customizability as a userspace component, but with the security, fairness, and control of the kernel over the resources.
Keywords: OS design, Memory Management, IO, Performance
Thesis / IDP
| 2024 | Towards DBMS-aware Memory Management in Unikernels | Martin Lindbüchl (BSc) |
# Safe and Verified Unikernel Extensions
Unikernels specialize operating systems by tailoring the kernel code for a specific application at compile time. While the specialized library OS approach improves the bootup process, performance, and migration costs, unikernels lack run-time extensibility, e.g., debugging, monitoring, re-configuration, and system management. Consequently, unikernels present a fundamental trade-off between the slimness of the image size at the compile time vs. the flexibility of supported auxiliary functionality at the run-time.
This project aims to balance this trade-off by keeping the unikernel file system image as minimal as possible to solely support the application functionality in the “common case”, while providing “on-demand” extensibility for auxiliary tasks at run-time. Additionally we apply run-time hardening and verification mechanisms to maintain safety isolation within the extended unikernel.
Keywords: Virtualization, Unikernels, eBPF
Publication
- MorphOS: An Extensible Networked Operating System
Peter Okelmann, Ilya Meignan–Masson, Masanori Misono, Pramod Bhatotia
CoNEXT 2025
[Paper] [Presentation] [Code] - uIO: Lightweight and Extensible Unikernels
Masanori Misono, Peter Okelmann, Charalampos Mainas, Pramod Bhatotia
SoCC 2024
[Paper] [Presentation] [Code]
Thesis / IDP
| 2023 | UniBPF: Safe and Verifiable Unikernels Extensions | Kai-Chun Hsieh (MSc) |
| 2023 | Extending Unikernels with a Language Runtime | Vanda Hendrychova (MSc) |
| 2024 | Network Function Virtualization with UniBPF | Paul Zhang (BSc) |
| 2024 | Serverless computing in unikernels using eBPF code injection | Milen Vitanov (MSc) |
| 2025 | Online OS reconfiguration for Cloud DBMS | Hristina Yordanova Grigorova (MSc) |
Group Members
Related Teaching
| SoSe 2025, 2024 | Practical Course | Advanced System Programming |
| SoSe 2025, 2024 WiSe 2024/25, 2023/24 | Practical Course | System Programming |
| WiSe 2023/24 | Seminar | Operating Systems and Virtualization |



